Did you know that nearly 54 percent of companies experience a data breach each year? Data security is no longer a back-office concern but a core necessity for any organization that relies on sensitive information. Cyber threats are growing in both number and complexity, making strong safeguards essential for protecting customers, business reputation, and operational stability. Learn what it takes to create a secure environment and keep valuable data out of the wrong hands.
Table of Contents
- Defining Data Security and Its Importance
- Core Types of Data Security Measures
- Key Technologies and Implementation Strategies
- Compliance Requirements and Industry Standards
- Risks, Common Vulnerabilities, and How to Avoid Them
Key Takeaways
Defining Data Security and Its Importance
Data security represents the comprehensive set of strategies and practices designed to protect organizational data from unauthorized access, theft, and potential corruption. According to OpenStax, data security involves implementing targeted measures that ensure the confidentiality, integrity, and availability of critical information assets.
At its core, data security encompasses both digital and physical safeguards that shield sensitive information throughout its entire lifecycle. The NNLM highlights that protection mechanisms range from sophisticated encryption technologies to physical access controls, creating multiple layers of defense against potential security breaches.
The importance of robust data security cannot be overstated for modern organizations. Key reasons include:
- Protecting sensitive customer and corporate information
- Maintaining regulatory compliance across industries
- Preventing financial losses from potential data breaches
- Preserving organizational reputation and customer trust
- Mitigating risks associated with cyber threats and unauthorized data access
For organizations seeking to enhance their security questionnaire processes, understanding comprehensive data protection strategies is crucial. Explore our guide on effective security questions to strengthen your organizational security approach.
Core Types of Data Security Measures
Data security encompasses a range of sophisticated strategies designed to protect sensitive information from unauthorized access and potential breaches. According to Kent State LibGuides, core security controls include password protection, data encryption, data identifier separation, and secure transmission methods like Transport Layer Security (TLS).
Among these protective measures, encryption stands out as a fundamental technique for safeguarding critical information. As CISA explains, encryption transforms sensitive data into unreadable code, ensuring that only authorized personnel can access and interpret the information.
Key data security measures can be categorized into several critical domains:
- Network Security: Protecting data transmission channels
- Access Control: Restricting data access based on user privileges
- Authentication Mechanisms: Verifying user identities before data access
- Encryption Technologies: Converting data into secure, unreadable formats
- Backup and Recovery Systems: Ensuring data can be restored after potential incidents
Here’s a summary of key data security measures and their primary focus:
For organizations looking to enhance their comprehensive security approach, understanding the HIPAA Security Rule can provide additional insights into robust data protection strategies.
Key Technologies and Implementation Strategies
Effective data security requires a strategic approach that combines advanced technologies and proactive implementation techniques. According to CISA, critical strategies include implementing encryption for data at rest and in transit, utilizing strong password protocols, and maintaining consistent data backup procedures.
Technological foundations play a crucial role in comprehensive security frameworks. Kent State LibGuides emphasizes the importance of multiple layers of protection, including secure transmission protocols like Transport Layer Security (TLS), robust identifier separation techniques, and sophisticated encryption methodologies.
Key implementation strategies organizations should consider include:
- Developing comprehensive security policies
- Conducting regular risk assessments
- Implementing multi-factor authentication
- Creating robust incident response plans
- Providing continuous employee security training
- Establishing regular system vulnerability scans

For organizations seeking to streamline their security processes and enhance questionnaire management, understanding the HIPAA Security Rule can provide valuable insights into structured security approaches.
Compliance Requirements and Industry Standards
Navigating the complex landscape of data security compliance requires a strategic and comprehensive approach to managing organizational information. According to EDUCAUSE, organizations must implement data classification policies that categorize information into distinct levels - public, confidential, and sensitive - with each category demanding specific security protocols and protective measures.
Internal governance frameworks play a critical role in establishing robust compliance mechanisms. As highlighted by the U.S. Department of Education, standards such as the U.S. Government Accountability Office’s Green Book provide essential guidelines to ensure effective data management and regulatory adherence.
Key compliance considerations for organizations include:
- Identifying applicable regulatory requirements
- Developing comprehensive data protection policies
- Implementing regular compliance audits
- Maintaining detailed documentation of security practices
- Ensuring transparent reporting mechanisms
- Conducting periodic risk assessments
- Training employees on compliance protocols
For organizations seeking deeper insights into regulatory compliance, understanding the HIPAA Security Rule can provide valuable context for developing robust security frameworks.
Risks, Common Vulnerabilities, and How to Avoid Them
In the ever-evolving digital landscape, organizations face increasingly sophisticated cybersecurity threats that can compromise sensitive data and disrupt business operations. According to UCSC Institute, ransomware attacks and data breaches represent critical risks that can lead to substantial operational disruptions and irreparable damage to customer trust.
Digital.gov emphasizes the importance of implementing robust identity, credential, and access management controls as fundamental strategies for preventing unauthorized system access and mitigating potential security vulnerabilities. Comprehensive web security requires a multilayered approach that anticipates and neutralizes potential threats before they can penetrate organizational systems.
Common data security vulnerabilities organizations must proactively address include:
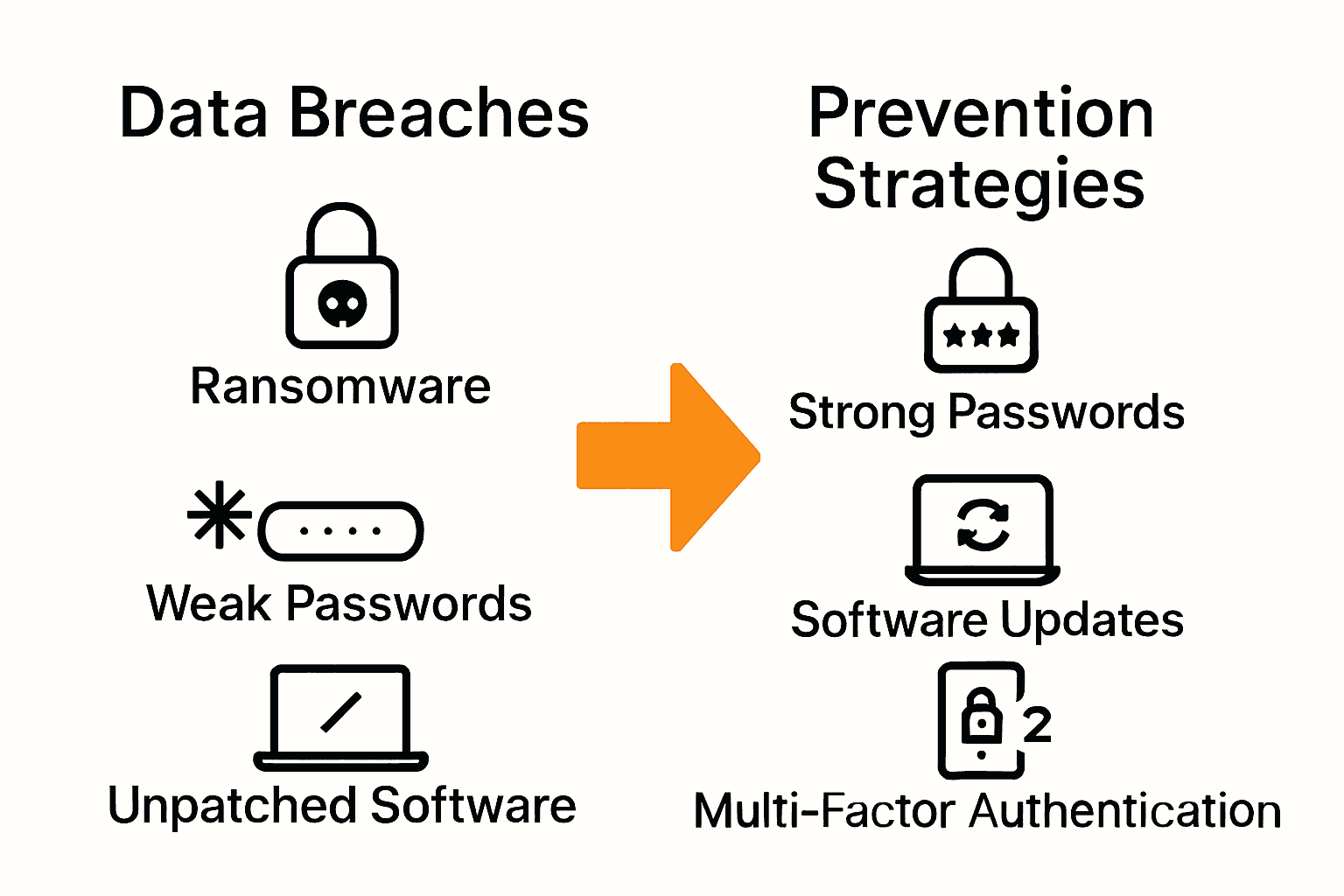
- Weak password protocols
- Unpatched software systems
- Insufficient access controls
- Inadequate employee security training
- Lack of multi-factor authentication
- Outdated security infrastructure
- Unsecured third-party vendor connections
To enhance vendor risk management strategies and develop a comprehensive approach to identifying potential security gaps, explore our guide to mitigating vendor management risks which provides actionable insights for protecting organizational assets.
Accelerate Your Data Security Compliance with Skypher’s AI-Driven Solutions
Managing data security best practices requires precision, efficiency, and seamless collaboration to protect your organization against risks like data breaches and compliance failures. The challenges outlined in the Complete Guide to Data Security Best Practices emphasize the need for robust authentication, encryption, and thorough risk assessments. These critical tasks often involve extensive security questionnaires that can slow down progress and drain valuable resources.

Skypher is designed to solve these exact pain points by offering an AI Questionnaire Automation Tool that rapidly streamlines and automates responses to complex security reviews. With support for multiple file formats and integration with over 40 third-party risk management platforms, Skypher enables your team to complete hundreds of questions in under a minute. Maximize productivity and maintain top-tier compliance with features like customizable Trust Centers and real-time collaboration. Don’t let manual security questionnaire processes hold your organization back. Take control today by visiting Skypher and discover how you can enhance your data protection strategy efficiently and confidently. Start automating your security questionnaire process now and see immediate improvements in accuracy and turnaround time with our innovative platform.
Frequently Asked Questions
What are the core principles of data security?
Data security is based on three core principles: confidentiality, integrity, and availability. These principles ensure that sensitive information is protected from unauthorized access, remains accurate, and is accessible when needed.
What are common types of data security measures?
Common data security measures include encryption, access control, authentication mechanisms, network security, and backup and recovery systems. Each measure is designed to address distinct aspects of data protection.
How can organizations enhance their data security practices?
Organizations can enhance their data security practices by developing comprehensive security policies, conducting regular risk assessments, implementing multi-factor authentication, and providing ongoing employee training on security protocols.
What are some risks and vulnerabilities related to data security?
Risks related to data security include ransomware attacks, data breaches, weak password protocols, unpatched software, and inadequate employee training. Addressing these vulnerabilities is crucial to maintaining strong data security.





