Staying ahead of cyber threats in fintech is a challenge for every organization. With phishing, data breaches, and advanced malware attacks on the rise, a single mistake can put sensitive financial data and customer trust at risk. It takes more than just technical solutions—your entire team needs to become part of the defense.
This guide delivers the practical steps and proven tactics you need to build real security awareness. You will discover how to recognize evolving phishing scams, manage passwords safely, protect confidential data, and respond decisively to incidents. Clear, actionable insights ahead will help you strengthen your fintech operations from the inside out.
Table of Contents
- 1. Introduction to Security Awareness and Its Importance
- 2. Recognizing Phishing Attempts in Daily Operations
- 3. Safe Data Handling and Confidentiality Practices
- 4. Effective Password Management and Authentication Tips
- 5. Incident Response Procedures for Financial Teams
- 6. Utilizing AI Tools for Automated Security Training
- 7. Continuous Improvement Through Feedback and Assessment
Quick Summary
1. Introduction to Security Awareness and Its Importance
Security awareness is the foundation of robust cybersecurity practices for fintech organizations. It represents a comprehensive approach to protecting digital assets by educating employees about potential risks and empowering them to make informed decisions.
In the rapidly evolving digital landscape, cybersecurity is no longer just an IT department responsibility. Every team member plays a critical role in maintaining an organization’s security posture. This means understanding potential threats, recognizing suspicious activities, and knowing how to respond appropriately.
Key components of security awareness include:
- Recognizing potential cyber threats
- Understanding personal and organizational security protocols
- Developing a proactive mindset toward digital safety
- Learning to identify and report potential security incidents
Security awareness transforms employees from potential vulnerabilities into active defenders of organizational data.
Fintech leaders must recognize that human error remains one of the most significant security risks. Comprehensive security management systems can help mitigate these risks by providing structured training and continuous learning opportunities.
Effective security awareness training goes beyond simple compliance. It creates a culture of security where every employee understands their role in protecting sensitive information. This approach reduces the likelihood of successful cyberattacks and minimizes potential financial and reputational damage.
Pro tip: Conduct regular simulated phishing exercises to help employees recognize and respond to potential social engineering attempts.
2. Recognizing Phishing Attempts in Daily Operations
Phishing represents one of the most prevalent and dangerous cybersecurity threats in modern financial technology environments. These sophisticated social engineering attacks aim to deceive employees into revealing sensitive information or compromising organizational security systems.
Phishing attempts can take multiple sophisticated forms, ranging from email impersonations to complex digital communications designed to exploit human psychology. Fintech leaders must train their teams to recognize and respond to these increasingly clever manipulation tactics.
Key indicators of potential phishing attempts include:
- Urgent or threatening language in communications
- Requests for immediate action or personal information
- Suspicious email addresses with slight misspellings
- Unexpected attachments or links
- Communications that create emotional pressure
Successful phishing detection requires constant vigilance and a skeptical approach to unexpected digital communications.
Modern phishing strategies have become remarkably advanced. Attackers now use highly personalized psychological manipulation techniques that can bypass traditional security awareness training. Understanding these nuanced approaches is critical for protecting organizational assets.
Financial technology professionals should implement security best practices that include rigorous verification protocols. This means establishing clear communication channels and creating standardized procedures for validating unexpected requests.
Employees must understand that legitimate organizations will never request sensitive information through unsecured channels. Training should emphasize the importance of independent verification through official contact methods.
Pro tip: Create a dedicated internal communication channel where employees can quickly report and verify suspicious digital communications without fear of reprisal.
3. Safe Data Handling and Confidentiality Practices
Data handling and confidentiality represent the cornerstone of cybersecurity in financial technology organizations. Protecting sensitive information is not just a technical requirement but a fundamental business and ethical responsibility.
Data breaches can devastate organizational reputation and create massive financial and legal risks. Fintech leaders must establish comprehensive protocols that transform every employee into a proactive data protection guardian.
Key principles of safe data handling include:
- Implementing strict access controls
- Encrypting sensitive information
- Limiting data sharing to authorized personnel
- Developing clear classification standards
- Creating robust data retention and deletion policies
Confidentiality is not about perfect security but consistent vigilance and strategic risk management.
Financial technology organizations must develop nuanced approaches to data protection that go beyond basic compliance. Understanding security rule implications helps create more comprehensive protection strategies.
Effective data handling requires multiple layers of protection. This means combining technological solutions with comprehensive employee training. Organizations should establish clear communication channels that enable staff to report potential vulnerabilities without fear of reprisal.
Advanced data protection strategies involve continuous education and adaptive security protocols. Regular training sessions that simulate real-world scenarios can help employees internalize best practices and develop an instinctive approach to information security.
Pro tip: Implement a quarterly data handling review process that includes anonymized case studies of potential security breaches to keep team awareness sharp and engagement high.
4. Effective Password Management and Authentication Tips
Password management represents a critical defense mechanism in protecting organizational digital assets. Financial technology leaders must recognize that weak authentication practices create significant vulnerabilities in cybersecurity infrastructure.
Authentication is more than just passwords. Modern security requires multifaceted strategies that combine technological solutions with intelligent human practices.
Key password management principles include:
- Using complex, unique passwords for each system
- Implementing multifactor authentication
- Avoiding predictable password patterns
- Regularly updating credentials
- Using password management tools
- Enabling login attempt monitoring
Passwords are the first line of defense against unauthorized system access.
Fintech organizations should develop robust authentication protocols that go beyond traditional username and password combinations. Understanding effective security questions can significantly enhance verification processes.
Biometric and behavioral authentication technologies are increasingly becoming standard in high-security environments. These advanced approaches analyze unique user characteristics like typing patterns, mouse movement, and device interaction to provide additional security layers.
Training employees to recognize social engineering tactics that target authentication systems is equally important. Attackers often exploit human psychology to bypass technical security measures through manipulation and deception.
Pro tip: Implement a quarterly password rotation policy that includes mandatory security awareness training to reinforce best practices and keep authentication protocols dynamic.
5. Incident Response Procedures for Financial Teams
Incident response represents a critical cybersecurity capability that determines an organization’s ability to minimize damage and recover quickly from potential security breaches. Financial technology teams must develop systematic approaches that transform potential crises into manageable challenges.
Rapid and coordinated response prevents escalation of security incidents and protects organizational assets. A well-structured incident management framework can significantly reduce financial and reputational risks.
Key components of an effective incident response procedure include:
- Establishing clear communication protocols
- Defining specific roles and responsibilities
- Creating detailed escalation pathways
- Implementing real-time tracking mechanisms
- Developing comprehensive documentation standards
- Conducting regular simulation exercises
Speed and precision are paramount in managing cybersecurity incidents effectively.
Financial organizations must develop adaptive strategies that account for the unique complexities of their technological ecosystems. Risk management approaches play a crucial role in creating resilient response frameworks.
Incident classification and triage processes are fundamental to effective response strategies. Teams should categorize potential security events based on their potential impact and develop nuanced response protocols that match the severity of each scenario.
Modern incident response requires cross-functional collaboration. This means breaking down traditional organizational silos and creating integrated teams that can respond quickly and comprehensively to emerging threats.
Pro tip: Develop a centralized incident response dashboard that provides real-time visibility and enables immediate communication across different organizational teams during potential security events.
6. Utilizing AI Tools for Automated Security Training
Artificial intelligence represents a transformative approach to modernizing security awareness training in financial technology organizations. AI-powered tools can dynamically adapt learning experiences to address specific organizational vulnerabilities and individual knowledge gaps.
AI transforms passive training into interactive experiences. By leveraging machine learning algorithms, these tools create personalized learning pathways that continuously evolve based on user interactions and performance.
Key advantages of AI-driven security training include:
- Personalized learning experiences
- Real-time performance tracking
- Adaptive difficulty levels
- Continuous knowledge assessment
- Scalable training solutions
- Instant feedback mechanisms
Intelligent training systems turn security education from a compliance requirement into a strategic organizational capability.
Financial technology leaders can now implement automated compliance solutions that dramatically reduce human error and training time. These advanced systems analyze individual learning patterns and create targeted interventions.
Predictive analytics enhance training effectiveness by identifying potential knowledge gaps before they become critical vulnerabilities. AI tools can simulate realistic cybersecurity scenarios that test and improve employee response capabilities.
Successful implementation requires a strategic approach that balances technological capabilities with human learning psychology. Organizations must view AI training tools as collaborative partners that augment existing training methodologies.
Pro tip: Implement a quarterly AI-powered skills assessment that provides granular insights into team cybersecurity readiness and identifies precise areas for targeted training interventions.
7. Continuous Improvement Through Feedback and Assessment
Continuous improvement represents the cornerstone of effective security awareness programs in financial technology organizations. By establishing systematic feedback mechanisms, leaders can transform training from a static compliance requirement into a dynamic learning ecosystem.
Feedback drives meaningful organizational growth. Regular assessment allows teams to identify knowledge gaps, emerging threats, and opportunities for targeted skill development.
Key components of an effective continuous improvement strategy include:
- Implementing regular skills assessments
- Creating anonymous reporting channels
- Developing adaptive training modules
- Tracking individual and team performance metrics
- Conducting periodic security simulations
- Encouraging open communication about potential vulnerabilities
Successful security awareness is a journey of constant learning and refinement.
Financial technology leaders can leverage security questionnaire automation tools to streamline assessment processes and generate actionable insights.
Quantitative and qualitative feedback mechanisms provide comprehensive understanding of organizational security readiness. This means combining hard performance data with nuanced employee perspectives to create holistic improvement strategies.
Effective assessment goes beyond simple testing. It involves creating a psychologically safe environment where employees feel comfortable reporting potential issues and sharing insights without fear of punishmro tip: Develop a quarterly security awareness scorecard that visualizes team progress, highlights improvement areas, and celebrates individual and collective security achievements.
Below is a comprehensive table summarizing the key insights, strategies, and guidelines discussed throughout the article about security awareness in fintech organizations.
Strengthen Your Fintech Security with AI-Powered Automation
The article highlights seven crucial security awareness trainings every fintech leader needs to reduce human errors and enhance incident response. With phishing attempts, safe data handling, and authentication challenges growing more sophisticated, maintaining a proactive security culture can be overwhelming. Skypher’s AI Questionnaire Automation Tool transforms this complex training and assessment process by streamlining security reviews and accelerating compliance efforts while improving accuracy and collaboration.
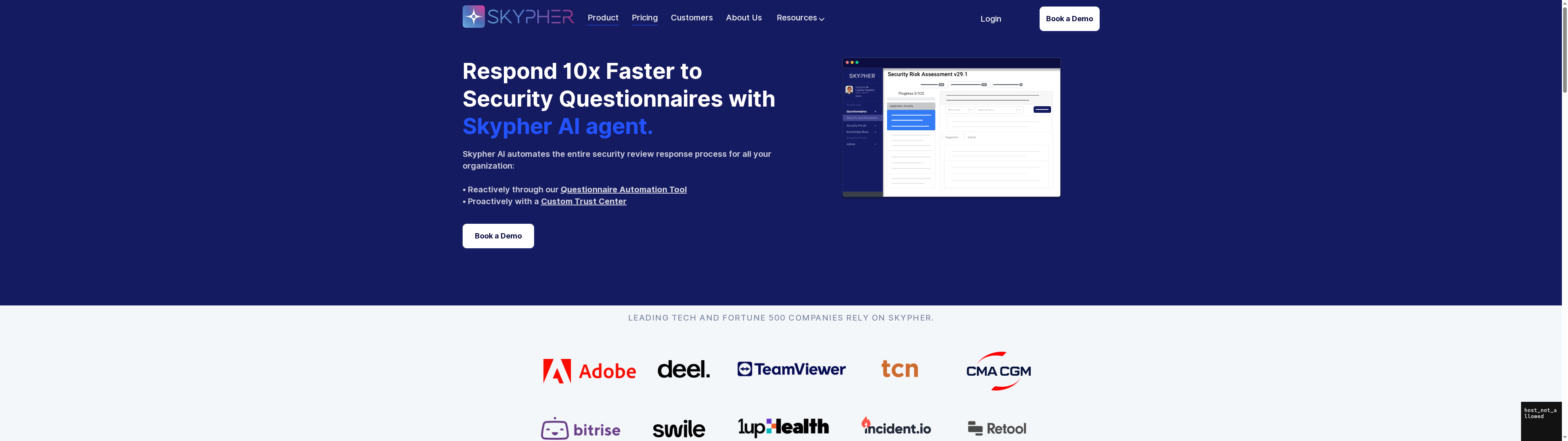
Take control of your organization’s security posture today by leveraging Skypher’s AI-driven platform. Benefit from real-time integrations with over 40 third-party risk management platforms and tools like Slack and ServiceNow to enhance communication and quick incident responses.
Visit https://skypher.co now to discover how our custom Trust Center and automated workflows can empower your team to stay vigilant and ready. Don’t wait until a costly breach occurs. Explore Skypher’s solutions and start reducing risk while increasing operational efficiency now.
Frequently Asked Questions
What are the key components of security awareness training for fintech leaders?
Effective security awareness training includes recognizing potential cyber threats, understanding security protocols, and developing a proactive mindset toward digital safety. To get started, evaluate your current training programs and incorporate hands-on exercises like simulated phishing tests within the next 30 days.
How can I improve employee recognition of phishing attempts in our organization?
Train employees to identify indicators of phishing, such as urgent communication or suspicious attachments. Conduct regular training sessions and simulated phishing attacks to enhance skills and awareness on a monthly basis.
What strategies should be implemented for safe data handling in fintech companies?
Establish strict access controls, encrypt sensitive information, and limit data sharing to appropriate personnel. Review current data handling policies and implement necessary changes within the next quarter to ensure consistent protection of sensitive data.
How can we ensure effective password management across our finance team?
Implement multifactor authentication and require the use of unique, complex passwords for all systems. Enforce a quarterly password update policy and provide training on effective password practices immediately.
What steps are essential for creating an incident response plan in financial technology?
Define roles and responsibilities, create clear communication protocols, and conduct regular simulation exercises. Begin developing your incident response plan within the next month, focusing on collaboration across all departments.
How can AI tools enhance security awareness training for our team?
AI tools personalize learning experiences and provide real-time feedback to employees. Start integrating AI into your training programs by researching available solutions and pilot-testing one within 60 days to assess its effectiveness.





